ARHS Spikeseed
cloud computing blog.
Our latest publications related to cloud
-
Gokdag Goktepe
OAuth 2.0 Authorization Code Flow & AWS Cognito
The previous article introduced the OAuth 2.0 protocol, highlighting distinctions between authentication and authorization. OAuth 2.0, an industry-standard protocol, was discussed in the context of cloud-native applications, addressing security concerns...
Read More -
Charles Guebels
AWS European Sovereign Cloud
Recently AWS announced that it was working on a European Sovereign Cloud, this is a good opportunity to discover a little more about what is hidden behind this term and...
Read More -
Dimitri Appriou
Effective secrets management in AWS
Today, secrets are used everywhere. Being the key to infrastructures and the data they are holding, a compromised secret can lead to security breaches of catastrophic proportions. Consequently, securing secrets...
Read More -
Yohan Beschi
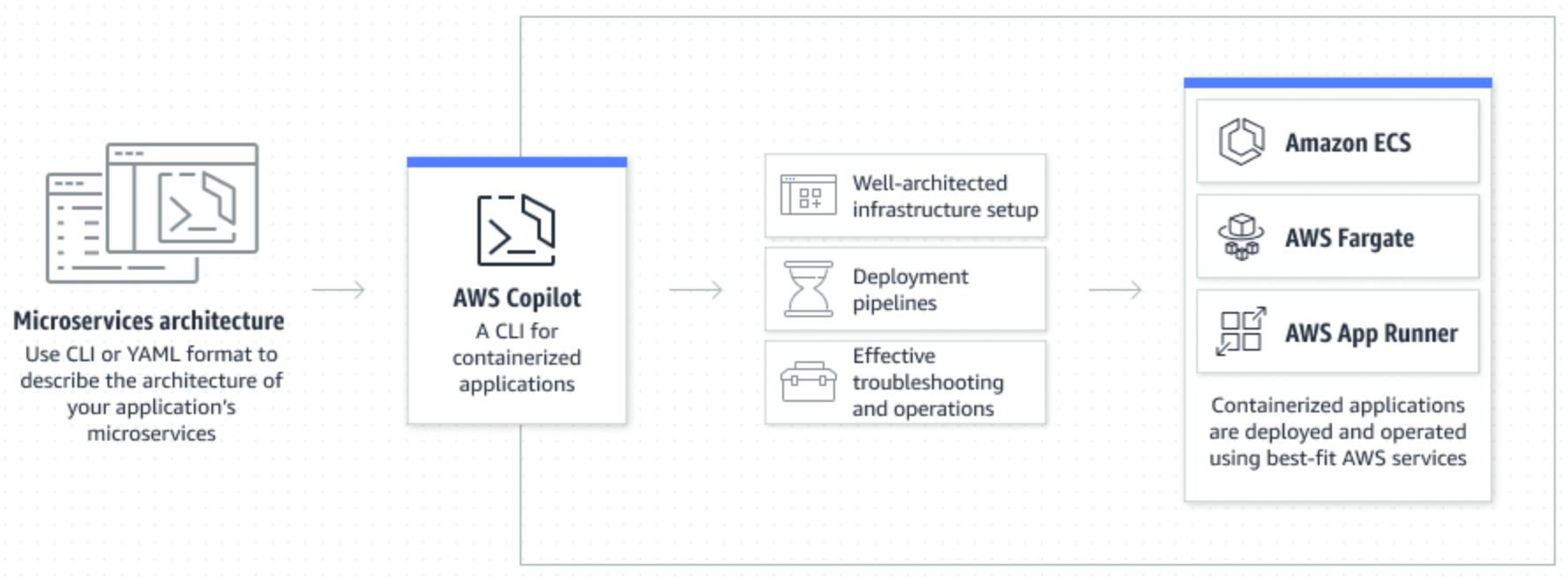
AWS Copilot, a friend that we all need
Sometimes we want to quickly deploy a container without the hassle of Infrastructure as Code. It can be because, we have limited AWS or infrastructure knowledge and we want to...
Read More -
Pierre Renard
Accelerate your Lambda functions with SnapStart
The cloud is a wonderful enabler to quickly create deploy and run a new application. In the early age, the cloud was only provided hosting services and then quickly provides...
Read More -
Pierre Renard
AWS re:Invent 2022 - Top 10 news
It’s the end of the year and like Santa, AWS comes fully-loaded with new services and features to Las Vegas at re:Invent.
Read More
Now it’s your turn!
Schedule a 1-on-1 with an ARHS Cloud Expert today!