Charles Guebels
Compliance reporting with Prowler

Following on from our blog post about Steampipe, this article presents the open-source compliance reporting tool named Prowler. As we have already did for Steampipe, we will see how to install it, configure it to generated desired reports and list the main pros and limitations of this tool. As a commercial version of Prowler also exists, we will see the main differences compared to the free version.
Testing environment setup
In this blog post, we will use the same testing environment as for our Steampipe blog post. It means that we will use a Cloud9 environment running with a specific IAM role.
If you have already followed the Steampipe setup instructions, you can reuse the same Cloud9 environment. Otherwise follow the instructions below:
- For the IAM role: https://blog.spikeseed.cloud/war-steampipe/#iam-role
- For the Cloud9 environment: https://blog.spikeseed.cloud/war-steampipe/#cloud9-configuration
Once this is done, you are ready to start configuring your Cloud9 environment to install Prowler.
Cloud9 environment configuration
Run the command below to install all the prowler prerequisites. Prowler will be installed using a Python package in a pip environment. Other possible installation methods are documented in this page.
1
2
3
4
5
6
7
8
9
10
11
12
curl -s https://pyenv.run | bash 1>/dev/null 2>&1
echo 'export PYENV_ROOT="$HOME/.pyenv"' >> ~/.bashrc
echo 'command -v pyenv >/dev/null || export PATH="$PYENV_ROOT/bin:$PATH"' >> ~/.bashrc
echo 'eval "$(pyenv init -)"' >> ~/.bashr
source ~/.bash_profile
source ~/.bashrc
pyenv install 3.9.16
pyenv global 3.9.16
python -m ensurepip --upgrade --user
python -m pip install --upgrade pip
source ~/.bash_profile
source ~/.bashrc
Prowler installation
Once all the prerequisites are installed, it is easy to install Prowler:
1
2
3
python -m pip install --upgrade prowler
echo -e "\n# Prowler setup\nalias prowler=\"python -m prowler\"" >> ~/.bashrc
source ~/.bashrc
To verify that Prowler is installed correctly you can run the command below:
1
prowler --version
Generate compliance reports
Compliance reporting is the core functionality of Prowler, the list of compatible compliance frameworks can be found in this page.
In this article we will work with the aws_well_architected_framework_security_pillar compliance framework, corresponding to the AWS Well-Architected security pillar.
The HTML report can be generated using the command below:
1
prowler aws -f eu-north-1 --output-modes html -F prowler-report-1 --compliance aws_well_architected_framework_security_pillar_aws
The full list of CLI parameters can be found in the official documentation. Below is the description of parameters used in the previous command:
- aws: It is the name of the cloud provider.
- filter-region: This parameter allows to generate the compliance report by only analyzing the resources of a specific region or list of regions.
- output-modes: This parameter specifies in which format we want to generate the report. The formats CSV, JSON, HTML and JSON-ASFF are available.
- output-filename: This parameter allows to give a name to the generated report.
- compliance: This parameter allows to specify the name or the list of compliance framework names. If several compliance frameworks are chosen, the report merges the results from all frameworks.
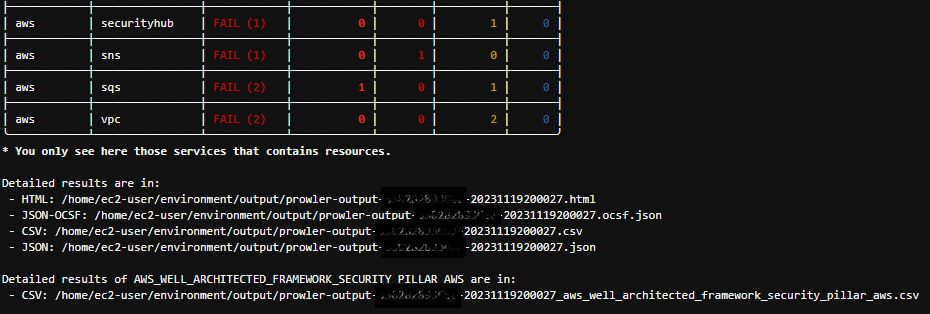
When executed, the command below produces a terminal output as in the screenshot below:
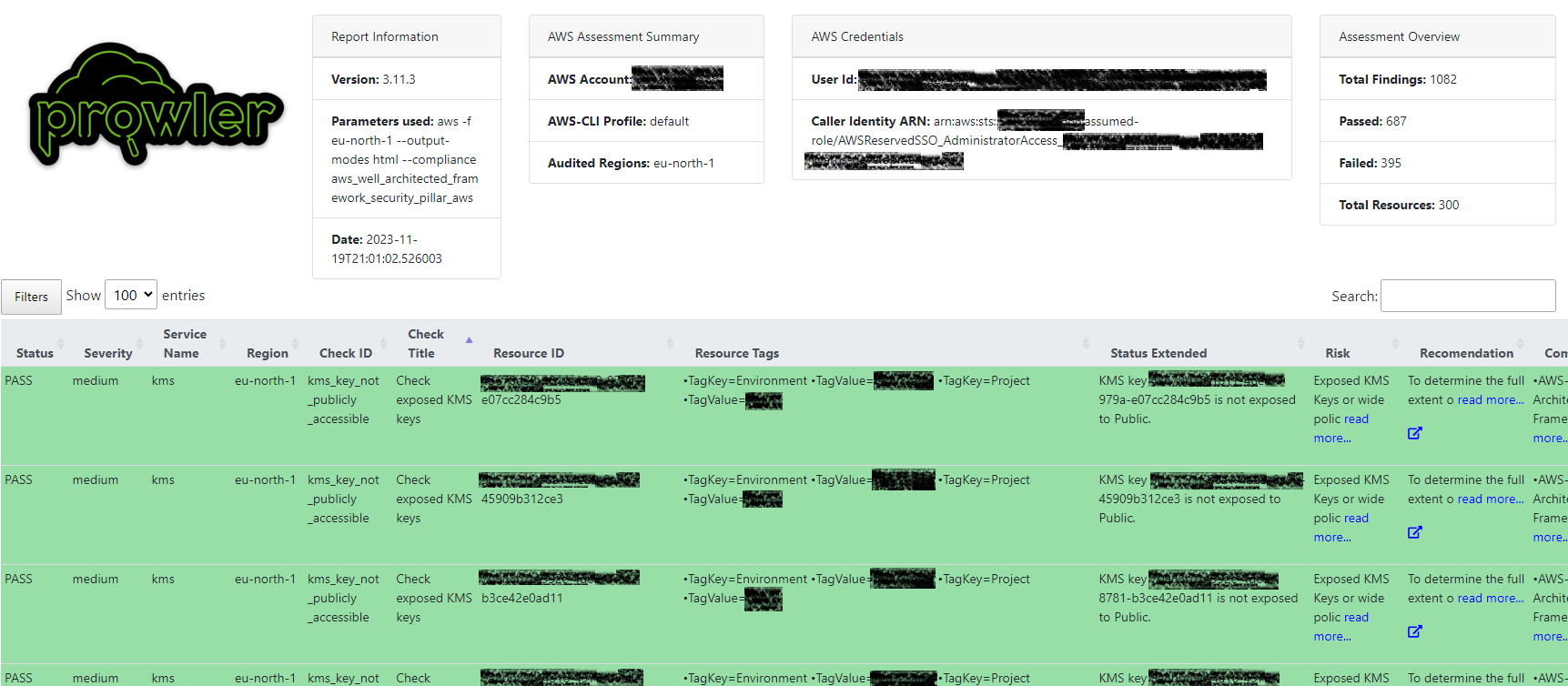
To open the generated HTML file in Cloud9 we need to right-click on the file name and select “Preview”. A Prowler report example is visible on the screenshot below.
(Click to enlarge the picture)
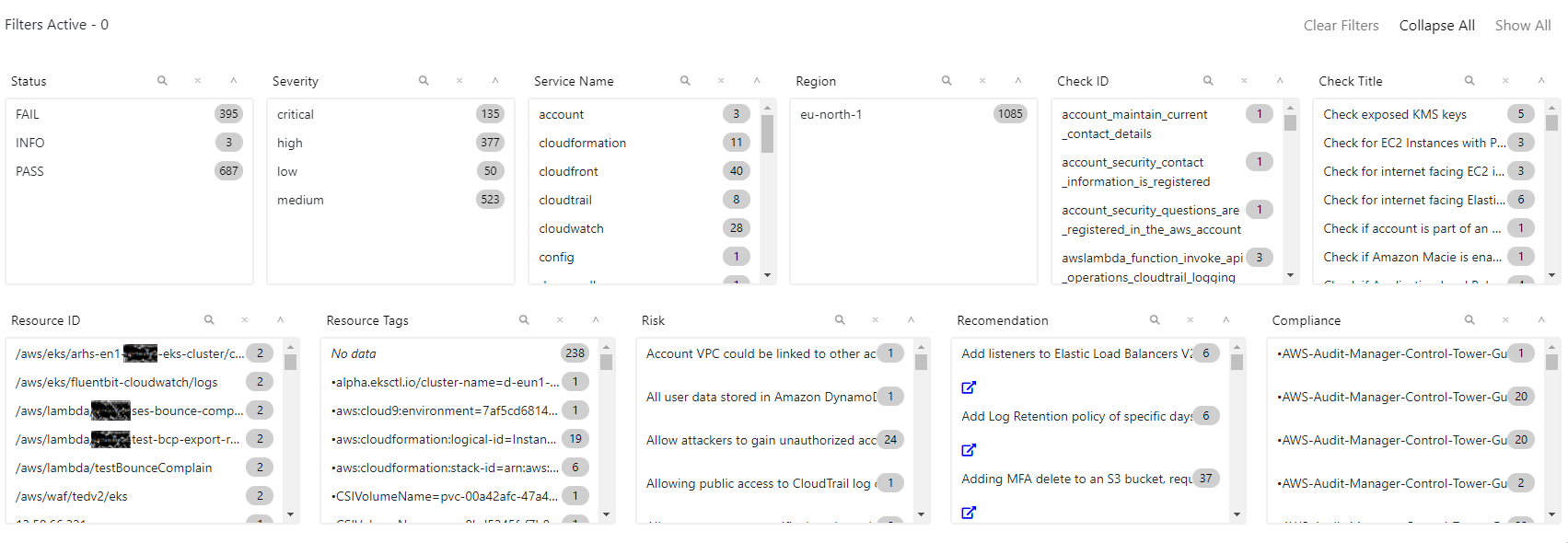
As we can see, this HTML report is clickable, we can for example, sort the results per column or define advanced filters using the Filters button. The screenshot below shows the content of the filtering configuration page:
(Click to enlarge the picture)
Prowler comes with additional CLI parameters useful to reduce the reporting scope. Below we can find a non-exhaustive list:
- Reduce the report to specifics services: The parameter services is able to do that:
1
prowler aws --services s3 ec2 kms - Exclude services from reporting: The parameter excluded-services is able to do that:
1
prowler aws --excluded-services acm kms - Reduce the report to specific checks: The parameter checks allows to restrict the report to only some checks.
1
prowler aws --checks s3_bucket_public_accessThe list of possible checks can be found thanks to the list-checks parameter:
1
prowler aws --list-checks - Exclude specific checks form the report: It is the use of the excluded-checks parameter:
1
prowler aws --excluded-checks s3_bucket_public_access - Reduce the report to specific resources tags: The parameter resource-tags allows to restrict the report to only some resources with the specified AWS tags:
1
prowler aws --resource-tags Team=team-a Env=Prod
- Exclude the unused services from the report: Thanks to the parameter ignore-unused-services, it is possible to remove the findings related to unused AWS services:
1
prowler aws --ignore-unused-services
Generate inventory report
Another feature of Prowler is the ability to list the existing resources in an AWS account. It can be particularly useful to ensure that no resources are yet running on a specific region like in the example below:
1
prowler aws --quick-inventory --filter-region eu-north-1 -F inventory
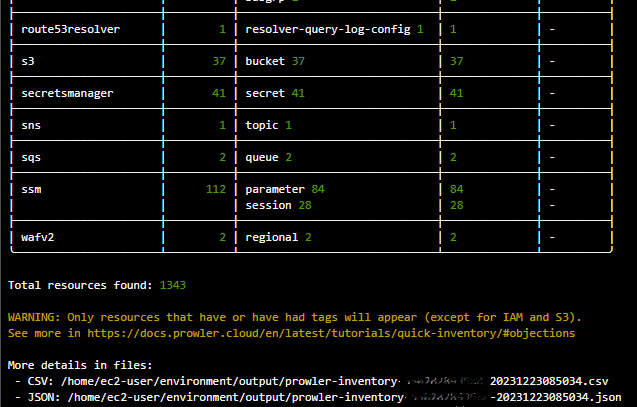
The command below generates a report in the terminal as in the screenshot below. Addtionally, the report is also generated in CSV and JSON formats.
Pro version
A commercial version of Prowler exists under the name ProwlerPro. According to the documentation, the main differences between the open-source version and the professional one are:
- Beautiful visualizations;
- Faster resources scanning;
- SaaS model;
- Continuous detection;
- Findings custom prioritization.
More information about this version can be found on the official website: https://prowler.pro.
Advantages
We can attribute several advantages to using Prowler, here are some one of them:
- Open-source tool;
- Complete free version available even if a commercial version exists;
- Many parameters to reduce the report scope;
- Multi-regions and multi-accounts possible configuration;
- Multi-clouds (AWS, Azure, GCP);
- Possibility to implement custom checks;
- “Dynamic” HTML report.
Limitations
Despite the many advantages we can also find some limitations:
- It is not possible to exclude specific tagged resources, for the management of false positives for example;
- The AWS WAR compliance framework is only compatible with the reliability and security pillars.
Conclusion
As we have seen throughout the article, Prowler is an open-source compliance reporting tool having many parameters to reduce the scope of the reports to specific resources, regions, services, checks, AWS tags, etc.. The installation, configuration and execution are very easy. Even if a commercial version exists, core features are available in the free version.